Security Assertion Markup Language (SAML) is an XML-based framework for enabling authentication through a third party identity provider or in-house single sign-on application.
SAML comes in handy for organizations which use multiple applications or services and need a single source to manage member activity. Instead of creating multiple credentials for different applications, with SAML you can create one set of credentials per member and allow them to access multiple applications.
This feature is available only on Scale and Enterprise plans. To know more, visit our plans and pricing page.
SAML offers the ability to:
Team Member: Team Member is an employee of the organization, say, Acme Inc, and is an authorized user of Acme Inc's Chargebee User Interface.
Authentication: The verification mechanism that certifies an individual is the actual person they claim to be.
IdP: Identity Provider (IdP) is the platform or application that provides authentication for the member.
SP: Service Provider (SP) is the application that needs authentication for allowing access to the member. For the entirety of this doc, Chargebee is the Service Provider.
Login URL: This URL will take you to the IdP's login page asking for your credentials. Login URL is provided by your IdP and must be added in Chargebee while integrating.
X.509 Certificate: Chargebee accepts only X.509 Certificate to validate the authenticity of an IdP.
You can log in to Chargebee using one of the ways listed below:
Sign in via IdP
Sign in via Chargebee
Login using Chargebee URL
You can add Chargebee app in Okta using the steps below:
These are required and need to be pasted in your Chargebee User Interface while enabling SAML.
You can add Chargebee app in Onelogin using the steps below:
These are required and need to be pasted in your Chargebee User Interface while enabling SAML.
You can add Chargebee app in Microsoft's Azure Active Directory using the steps below:
Sign into your Microsoft Azure site(through portal.azure.com).
Go to Azure Active Directory > Enterprise applications > New application > Non-gallery application and add an application by naming it as "Chargebee".
Now, go to the newly created Chargebee application and select Single sign-on found on the left pane and select SAML.
Click edit against the Basic SAML Configuration section and enter
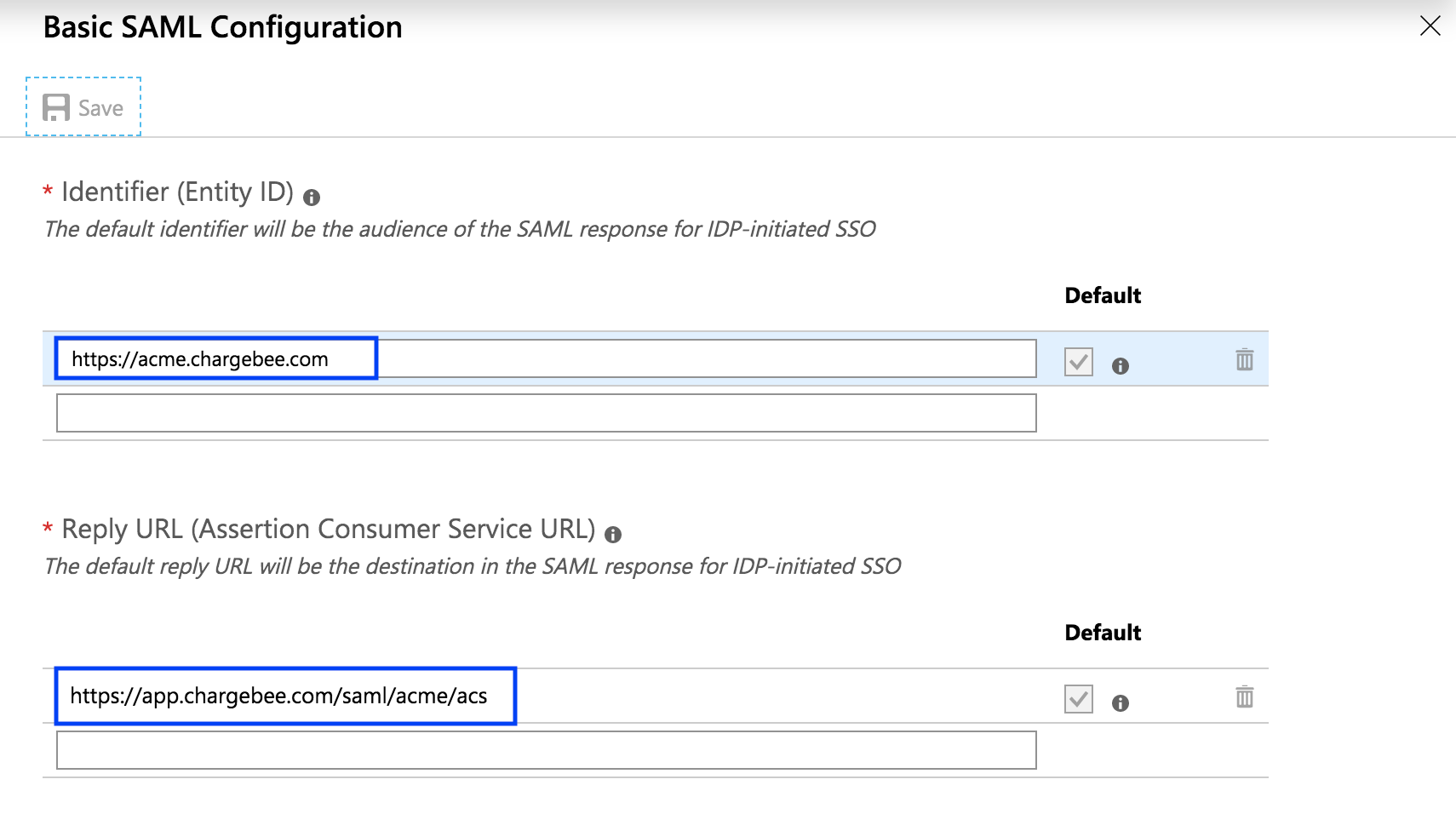
Scroll down to the Setup Chargebee section. Copy the Login URL and paste it in the field provided in Chargebee's SAML Configuration page.
In the SAML Signing Certificate section, Use the URL given against App Federation Metadata URL and copy the content present between the start and end tags of «X509Certificate». Paste it in Chargebee's SAML Certificate field.
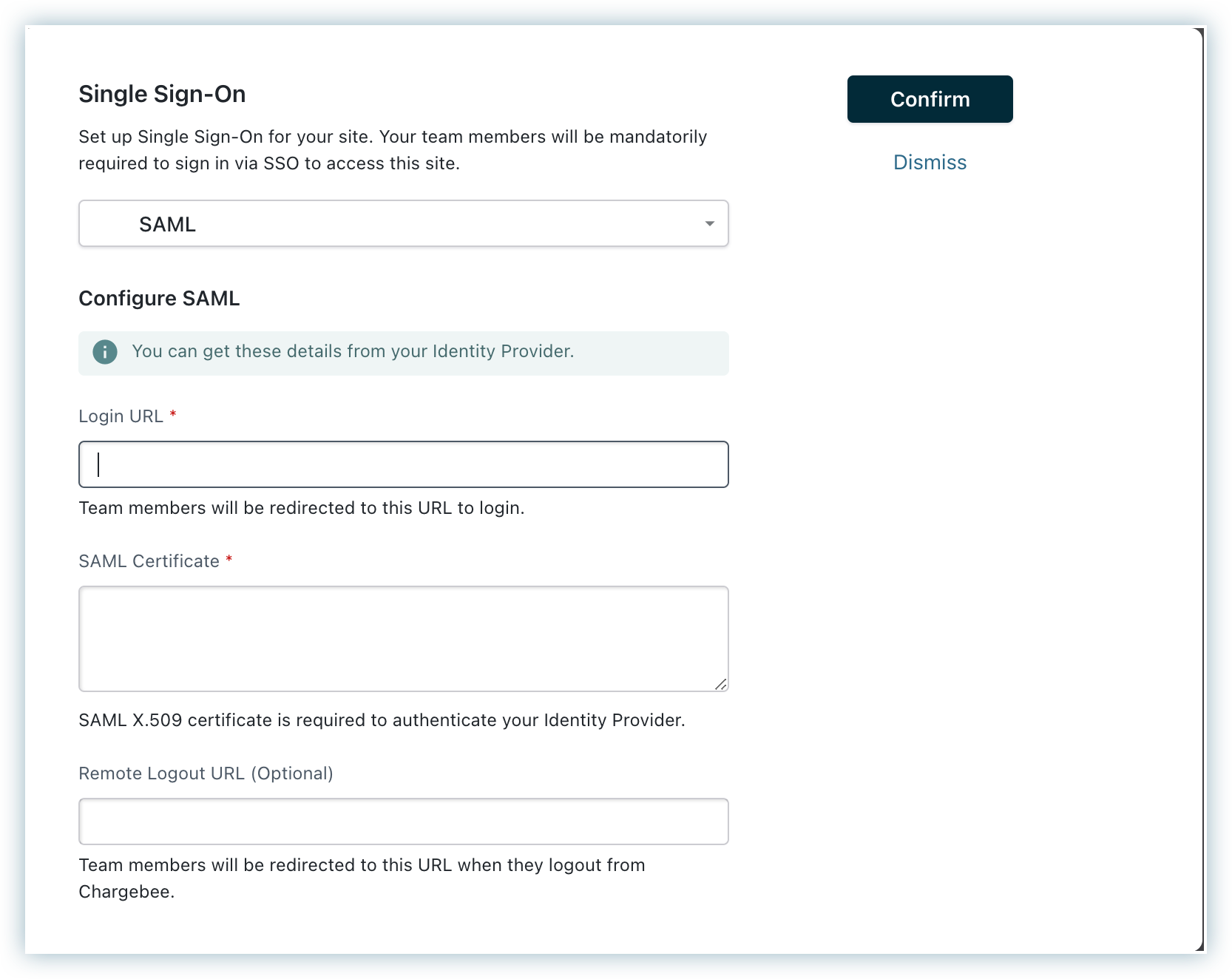
To disable SAML, go to Settings > Security and click Disable.
When you disable SAML in Chargebee, your team members will be notified that SAML has been disabled and they should sign in using custom credentials or Google SSO.
Your Team members will receive a system generated email during the following events:
1) What would happen if the team member's email is in the Chargebee site and not in IdP?
An error would occur while the team member enters the Chargebee site name and clicks on Sign In. Admin needs to add the team member's credentials in IdP to resolve this error.
2) What happens if you try to login via Single Sign-On when it is not enabled on your Chargebee site?
Chargebee will show the prompt "Single Sign-On is not enabled for this domain". SAML should be enabled to proceed, take a look at the steps to enable SAML.
3) How will team members with access to multiple Chargebee sites access Chargebee?
Team members having access to multiple Chargebee sites can easily switch between different sites using the option besides your Chargebee site name on the left-pane.
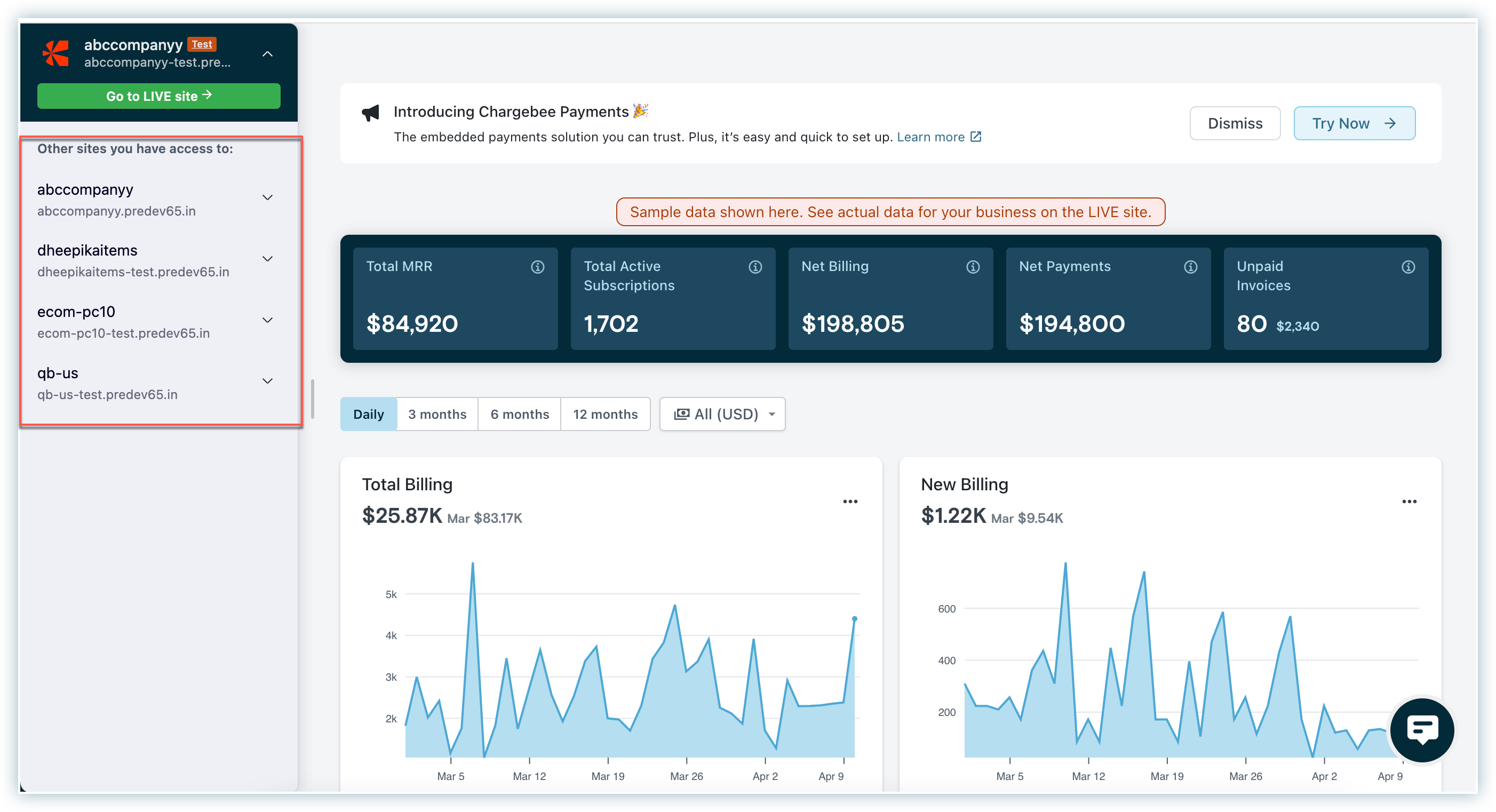
However, if the team members try to switch to a Chargebee site which does not have SAML enabled, they will be shown Chargebee's login screen. They can sign in using their custom credentials or via Google SSO.
4) How to generate a password when the team members don't have a password?
You can create a password by clicking on Forgot Password option in the login page and proceed.